LDAP is commonly used in Security realms as a source of authentication and authorization information. This tutorial will teach you two simple strategies for starting an LDAP Server in minutes in order to secure your Enterprise applications.
Option 1: Use an Embedded LDAP Server
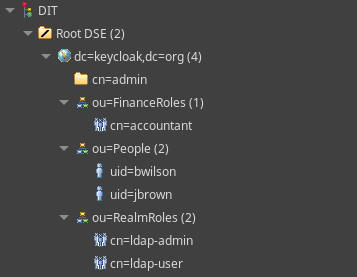
The first example is using an embedded ApacheDS LDAP server with preconfigured LDIF file with some example LDAP data (username, firstName, lastName, email), but also some custom attributes ( postal code, street).
In order to start the ApacheDS based LDAP server you just need the pom.xml file which contains a reference to the keycloak-util-embedded-ldap package:
<dependency>
<groupId>org.keycloak</groupId>
<artifactId>keycloak-util-embedded-ldap</artifactId>
<scope>test</scope>
</dependency>
Then, specify in your exec-maven-plugin which Java class to start and include in its System Properties the ldif file to be loaded:
<plugin>
<groupId>org.codehaus.mojo</groupId>
<artifactId>exec-maven-plugin</artifactId>
<configuration>
<mainClass>org.keycloak.util.ldap.LDAPEmbeddedServer</mainClass>
<classpathScope>test</classpathScope>
<systemProperties>
<systemProperty>
<key>ldap.ldif</key>
<value>ldap-example-users.ldif</value>
</systemProperty>
</systemProperties>
</configuration>
</plugin>
That beiing said, you can start the LDAP server as follows:
mvn exec:java -Pldap
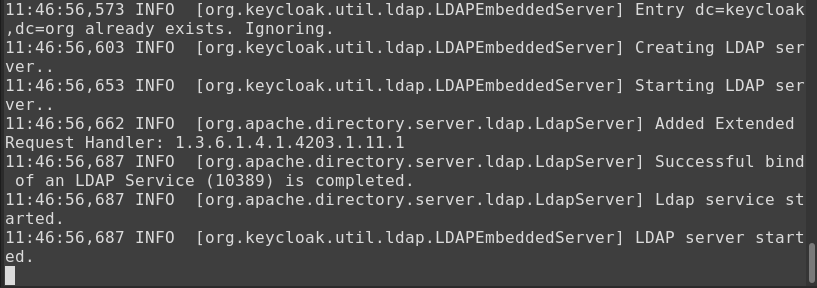
Here is the expected output:
You can find the pom.xml file and the ldif file in our Github repository: https://github.com/fmarchioni/mastertheboss/tree/master/ldap/embedded
Option 2: Use Docker to start LDAP
The second example we will show in this tutorial uses docker and OpenLDAP. The most common implementation of OpenLDAP is the osixia/openldap. You can start is as follows:
$ docker run --env LDAP_ORGANISATION="keycloak" --env LDAP_DOMAIN="keycloak.org" --env LDAP_ADMIN_PASSWORD="admin" osixia/openldap
Then, provided that you have installed LDAP Client tools, load the LDIF file using the ldapadd command. For example, in order to use the same example from keycloak:
$ ldapadd -f ldap-example-users.ldif -x -h 172.17.0.2 -p 389 -D "cn=admin,dc=keycloak,dc=org" -w "admin" -c adding new entry "dc=keycloak,dc=org" ldap_add: Already exists (68) adding new entry "ou=People,dc=keycloak,dc=org" adding new entry "ou=RealmRoles,dc=keycloak,dc=org" adding new entry "ou=FinanceRoles,dc=keycloak,dc=org" adding new entry "uid=jbrown,ou=People,dc=keycloak,dc=org" adding new entry "uid=bwilson,ou=People,dc=keycloak,dc=org" adding new entry "cn=ldap-user,ou=RealmRoles,dc=keycloak,dc=org" adding new entry "cn=ldap-admin,ou=RealmRoles,dc=keycloak,dc=org" adding new entry "cn=accountant,ou=FinanceRoles,dc=keycloak,dc=org"
You might have noticed that, the OpenLDAP docker imaged already created an entry for “dc=keycloak,dc=org”, therefore the first line of the ldif file was skipped in this case. Besides that, we have loaded the same structure with Users and Roles:
Option 3: Use a free Online LDAP Server
There are several online free LDAP servers which can be used in read-only mode to test your applications. My favuorite one is available at: https://www.forumsys.com
You can use the following settings to connect to the online server:
ldap.urls= ldap://ldap.forumsys.com:389/
ldap.base.dn= dc=example,dc=com
ldap.username= cn=read-only-admin,dc=example,dc=com
ldap.password= password
ldap.user.dn.pattern = uid={0}
Here is a snapshot from the list of users:
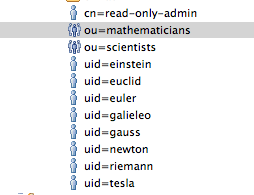
You can connect to individual Users (uid) or the two Groups (ou) that include:
ou=mathematicians,dc=example,dc=com
- riemann
- gauss
- euler
- euclid
ou=scientists,dc=example,dc=com
- einstein
- newton
- galieleo
- tesla
All user passwords are “password”.
That’s all. In this tutorial we have covered two strategies to start quickly an LDAP server for testing/developing applications using LDAP as repository
Found the article helpful? if so please follow us on Socials