In this article, we will explain how to enable Two Phase Authentication (2FA) with Keycloak. We will learn how to include the 2FA in the standard authentication flow and how to enforce it for a single user.
Two-factor authentication (2FA) is an additional layer of security that requires users to provide an additional form of authentication beyond their password when logging in. This can help protect against unauthorized access to accounts, even if an attacker has obtained a user’s password. Keycloak, an open-source identity and access management solution, offers support for 2FA through various authentication flows and mechanisms.
By default, Two-factor authentication is not enabled in the standard browser authentication flow of Keycloak. Let’s see how we can add it as part of a sample application
Prerequisites
- Install Keycloak distribution (or start is as Docker Image)
- Install a sample Realm on a Keycloak distribution. Check this article to learn more about it: Getting started with Keycloak powered by Quarkus
- Download a sample application to test the above Realm. For example: https://github.com/fmarchioni/mastertheboss/tree/master/bootable-jar/elytron-oidc-client-keycloak17
Next, we will move to the Two-factor authentication configuration
Enabling Two-factor authentication
Log in into the Admin Console and select “Authentication” in your Realm. This is the area where you can configure and manage different credential types.
Select the “Browser flow“:

This is a flow that is initiated when a user attempts to access a protected resource using a web browser. This flow typically involves redirecting the user to a login page, where they can enter their credentials. If the user’s credentials are valid, they will be granted access to the protected resource.
Here is an overview of the Browser flow:
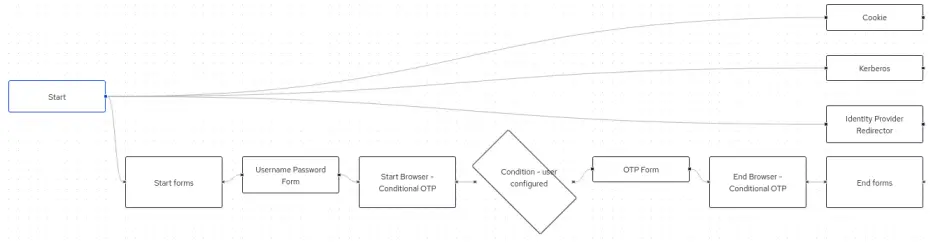
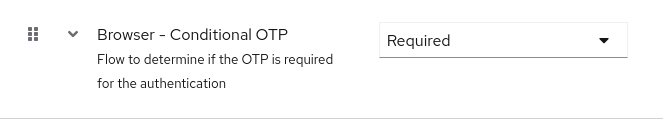
Within this flow, the Conditional OTP Form follows the standard username/password form. However, it is not a Required step by default. Make it Required by selecting the “Browser Conditional OTP” Combo:
Testing the 2FA mechanism
Firstly, you need to install an Application that is able to provide an OTP token. For example, you could install Google Authenticator or Free OTP on your Mobile.
Next, login in to the application using the credentials of the “wildfly-realm” which are customer-admin/admin.
After successful authentication, the OTP Token Form will display:
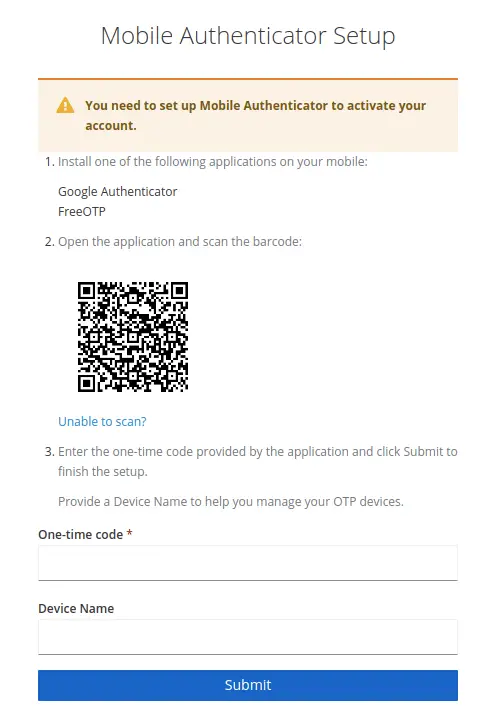
Next, scan the bar code with your Mobile OTP App.
Finally, collect the OTP Token for “wildfy-realm” in your App:

Enter the One-time code to complete the authentication.
Configuring the OTP Policy
To configure the OTP Policy for your Realm, follow these steps:
- Navigate to the Keycloak administration console and log in as an administrative user.
- In the left-hand menu, click on “Authentication” and then select the “OTP Policy” from the “Policies” tab.
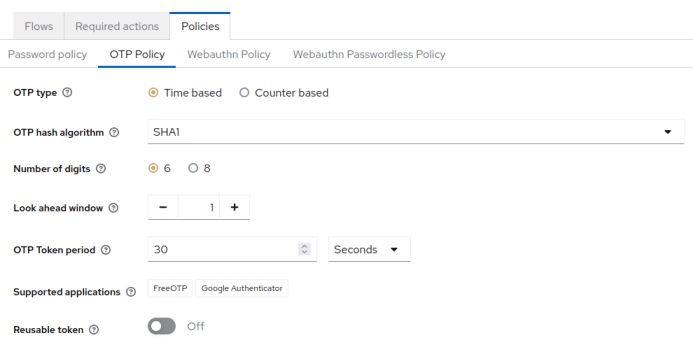
From there, you will be able to choose the OTP type (default is Time based), the Duration, the Supported applications and so on.
Enforcing Two-factor authentication for users
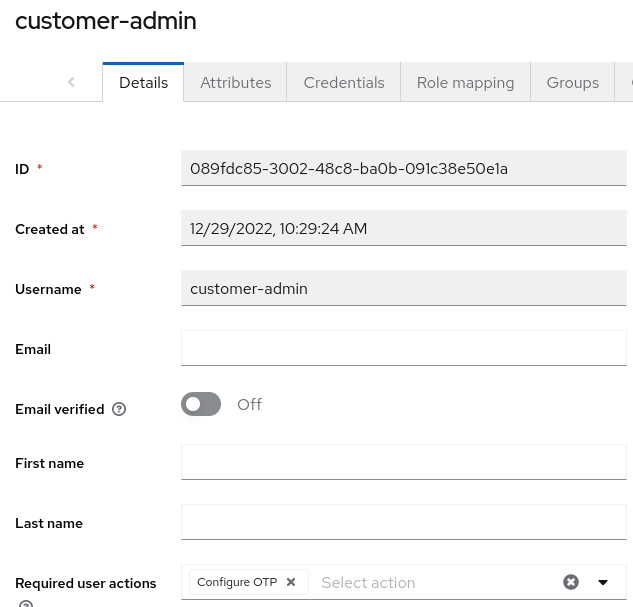
Finally, it is possible to enforce 2FA at user level in Keycloak. To do that, you can set the “Configure OTP” required action for the user. To do this, follow these steps:
- Firstly, navigate to the Keycloak administration console and log in as an administrative user.
- Next, in the left-hand menu, click on “Users” and then select the user you want to enforce 2FA for.
- Then, click on the “Actions” tab in the user’s profile page.
- Then, click on the “Add Required Action” button and select the “Configure OTP” option from the list.
- Finally, click on the “Save” button to save the changes.
Conclusion
Two-factor authentication (2FA) is an important security measure that adds an extra layer of protection to user accounts. Keycloak is an open-source software product that allows you to easily implement 2FA for your applications and services.
Found the article helpful? if so please follow us on Socials