The mod_cluster distribution includes a manager application which can be used to test your cluster topology and manage as well deployed applications across the cluster. In this tutorial we will show how to protect access to the mod_cluster_manager application with a password.
In order to protect our mod_cluster_manager application we will use a standard Apache directive named AuthUserFile directive which sets the name of a textual file containing the list of users and passwords for user authentication. We will use the utility htpasswd to maintain the password file for HTTP Basic Authentication.
Let’s see a concrete example. we will create an user “admin” with password “admin”:
$ htpasswd -c /etc/modclusterpassword admin New password: Re-type new password: Adding password for user admin
Here is the file created by htpasswd:
cat /etc/modclusterpassword admin:$apr1$8P17DkAF$bh1vedTcYCRf.lQ9y4Nl8/
Now let’s include a few directives into our mod_cluster_manager definition, so that a basic HTTP authentication will be requested for accessing our manager web application:
<Location /mod_cluster_manager> SetHandler mod_cluster-manager AuthType Basic AuthName "MCM" AuthUserFile /etc/modclusterpassword Require user admin Order deny,allow Deny from all Allow from all </Location>
As you can see, we are using the Apache AuthUserFile directive to specify the path to a file containing user names and password hashes for HTTP basic authentication.
Security note! Make sure that the AuthUserFile is stored outside the document tree of Apache. Do not put it in the directory that it protects. Otherwise, clients may be able to download the AuthUserFile.
Now restart Apache web server and try to access the mod_cluster_manager application:
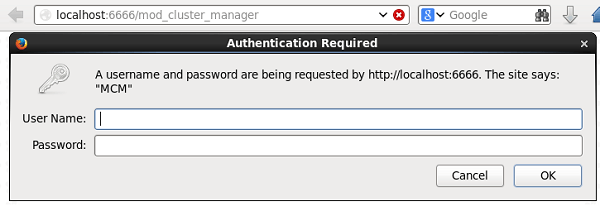
As you can see, now Apache Web server prompts for BASIC authentication.
Finally, keep in mind that HTTP basic authentication is not a secure method of protecting web applications. It is recommended to use more secure authentication methods, such as OAuth or SSH certificates, whenever possible.
Found the article helpful? if so please follow us on Socials